Insider Threat
Deliberate or accidental threat to an organisation’s security from anyone who has legitimate access to your organisation’s assets as they exploit their position for unauthorised purposes (so not just employees, but also contractors, partners and suppliers).

Successful insider threat programs proactively use a mitigation approach of detect and identify, assess, and manage to protect their organization.
The foundation of the program’s success is the detection and identification of observable, concerning behaviours or activities.
Insider Threat Indicators
Insider threat indicators are crucial to identifying potential risks within an organization.
Network anomalies and disgruntled employees are just a few examples of concerning behaviours that could signify a possible threat.
Trackable indicators such as unusual activity times, excessive data transfer, and accessing unusual resources should be closely monitored.
To enhance visibility, deploying a comprehensive solution that tracks employee actions and correlates data from multiple sources is recommended.
Leveraging technology can help identify malicious insiders or imposters and provide valuable insight into their actions.
Insider Threat Detection
Detecting insider threats can be challenging as they are often more difficult to identify and prevent than external attacks.
Traditional security solutions such as firewalls and intrusion detection systems are not designed to detect insider threats, making them invisible to these measures. In addition, malicious insiders who are familiar with an organization’s security measures can easily avoid detection.
To safeguard all assets, businesses must adopt a diversified insider threat detection strategy that goes beyond relying on a single solution. An effective detection system should incorporate the ability to monitor insider behaviour and alert on any anomalous activity.
At Fact360, we recognize that user behaviour analysis is paramount to protecting against insider threats. Our platform can seamlessly integrate with existing SIEM architecture, ensuring comprehensive and effective insider threat detection.
The FACT360 Platform
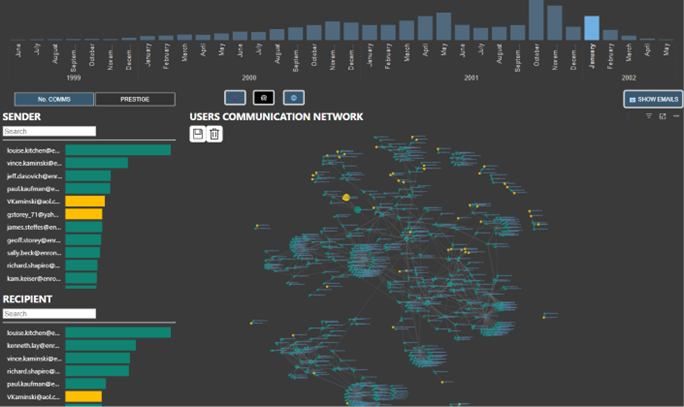
Our platform empowers businesses to effectively monitor communications at two levels, enabling them to proactively identify and prevent insider threats:
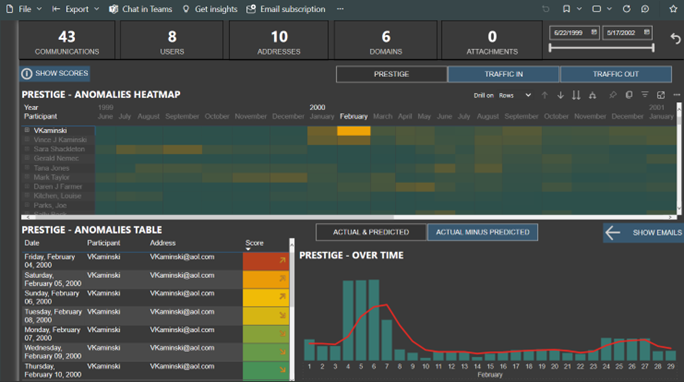
1. By forensically analysing communication traffic and identifying anomalous behaviour, alerts can be triggered for further investigation. This does not involve accessing the content of the communication at this stage.
2. Leveraging NLU-based analytics software, anomalies identified in step one can be thoroughly investigated to assess their potential threat level.
The primary value proposition of our platform is the ability to monitor human behaviour and identify potential threats before they materialize. With the addition of predictive analytics, organizations can significantly reduce reliance on incident response and proactively remove the threat before it occurs.
In Summary
In summary, Fact360 is the only platform dedicated to forensic analysis of communication networks and data, providing businesses with the following capabilities:
Ability to identify an individual's prestige in the organization or communication corpus, while remaining GDPR compliant.
Anomaly detection that detects changes in behaviour and alerts users, simplifying the identification and investigation of threats.
Contextualized Natural Language Understanding, offering guided search capabilities.
Full categorization of content in all communications, with context and meaning.
Comprehensive entity extraction, aiding in the isolation of key supportive intelligence.
Post-event investigation capabilities that accelerate investigations.
Near-real-time monitoring to prevent compliance breaches and detect changes in behaviour that could lead to future threats.
With Fact360, businesses can rely on cutting-edge technology to uncover insider threats and protect against data breaches, ensuring the security of their most critical assets.

FACT360’s solutions have fundamentally changed the way we operate as a business making us more efficient and generating better results for our clients.
OCULUS FINANCIAL INTELLIGENCE
Get in touch
If you would like further information please send us a message.
24 Picton House
Hussar Court
Waterlooville
Hampshire, PO7 7SQ
Registered Company No. 12503049
[email protected] or +44 (0)1483 667757